Windows Server Side Configuration
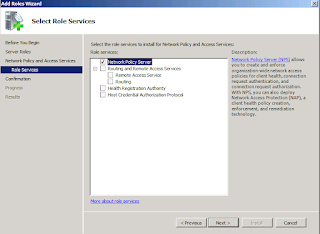
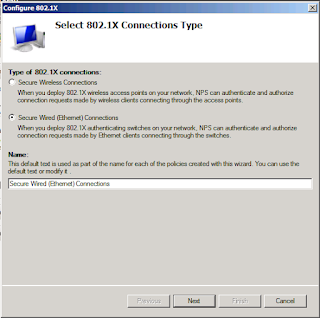
1- Install NPS Role on Windows Server 2008
2- Define the RADIUS clients
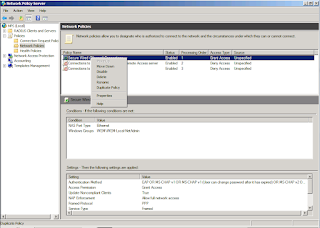
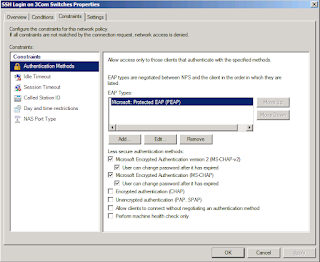
3- Modify Connection Request Policies using the Network Policy Server configuration Snap-in
5- Modify Standard Radius Attributes Dictionary on Windows Server 2008 by editing C:\Windows\System32\ias\dnary.xml to add SSH, FTP and Terminal under the Login-Service Attribute. The Standard RADIUS only allow for Telnet login by default, therefore the dictionary modification is needed in order to add, SSH, FTP and Terminal as login options under the standard RADIUS implementation.
6- Restart the Windows Server (Sometimes a Service Restart is not enough and a Server Restart might be required for the SSH option to show up among the standard RADIUS options)
7- Modify the Standard Radius Attribute inside the corresponding Network Policy to allow clients to log in using SSH.
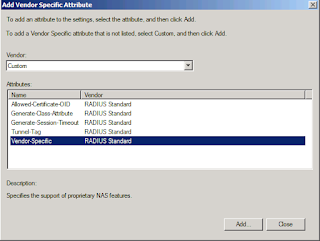
8- Modify the Vendor Specific Attribute to provide the corresponding User Access Level. Once the client connecting to the switch through SSH have been authenticate, the RADIUS server needs to tell the switch what access level is this user allowed. 3Com switches support the following access levels:
- - Level 0 (Attribute Number 1, Attribute Value 0) - 3Com-Visit
- - Level 1 (Attribute Number 1, Attribute Value 1) - 3Com-Monitor
- - Level 2 (Attribute Number 1, Attribute Value 2) - 3Com-Manager
- - Level 3 (Attribute Number 1, Attribute Value 3) - 3Com-Administrator
3Com Switch Side Configuration
1- Set up a Radius Scheme on 3Com
radius scheme domain_name
server-type extended
primary authentication IP_Address_Of_NPS_Server
primary accounting IP_Address_Of_NPS_Server
accounting optional
key authentication systems2006
key accounting systems2006
timer realtime-accounting 15
timer response-timeout 5
retry 5
user-name-format with-domain
nas-ip IP_Address_Of_Switch
calling-station-id mode mode2 uppercase
2- Set up a Domain and link it to the corresponding Radius Scheme
domain domain.local
scheme radius-scheme domain_name local
scheme lan-access radius-scheme domain_name
scheme login local
accounting lan-access radius-scheme domain_name
authentication login radius-scheme domain_name local
accounting login radius-scheme domain_name local
access-limit enable 60
idle-cut enable 20 2000
3- Set up the VTY interfaces to allow for ssh connections and to use the Radius Authentication Scheme
user-interface vty 0 4
authentication-mode scheme
4- Set up the SSH Server parameters
ssh-server source-ip ip_address
ssh server authentication-retries 5
5- Set up the SSH user that are allowed to log in using SSH. Ideally, I would like to specify a group, instead of a domain user (userid@wem.local), so that all users on that group are valid users for the 3Com switch, but I have not found the way to do that yet.
ssh user admin authentication-type password
ssh user admin service-type all
ssh user userid@domain.local authentication-type password
ssh user userid@domain.local service-type all
Troubleshooting
1- Check the Windows Server Event Viewer for Security , under Windows Logs. Verify the events are being logged as Audit Success.
2- Use Wireshark on the NPS Server and try to connect to the switch using SSH. Verify Radius parameters passed back from the NPS server to the Switch.
3- Use NTRadPing Test Utility freeware tool to test connectivity to the RADIUS server and check your parameters.
Recommendations
This procedure should be improved so that there is no need to define each user using the ssh user statement. Ideally only the AD user group should be used.
Implement the same authentication mecanism for the switch management web interface.
Comments are welcome !